Ransomed
Ransomed
Challenge Link:
https://cyberdefenders.org/blueteam-ctf-challenges/ransomed/
Scenario:
After a successful breach, A SOC analyst found an executable, but they could not know what it does, so they sent it to you for further analysis.
Questions:
After loading the sample to PEstudio we get can the answers of first 4 questions
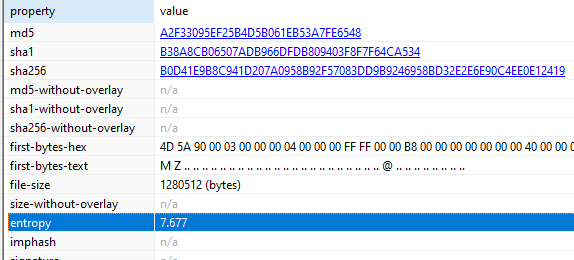
1 - What is the md5 hash of the file?
MD5: a2f33095ef25b4d5b061eb53a7fe6548
2- What is the value of entropy?
7.677
3- What is the number of sections?
4
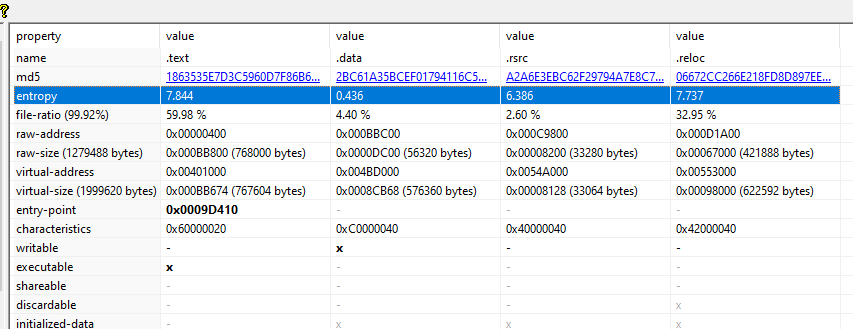
4- What is the entropy of the .text section?
7.844
5- What is the name of the technique used to obfuscate string?
I really can’t get the answer by my self and try to walk with the code line by line to get it, but I can’t.
I get hints from the challenge itself and some write-ups and I get that the technique is Stack Strings
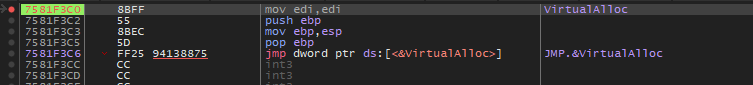
6- What is the API that used malware allocated memory to write shellcode?
Usually the API that used for allocating memory is VirtualAlloc, and we can confirm that by setting a breakpoint on it in x64dbg and see if it exists or not.
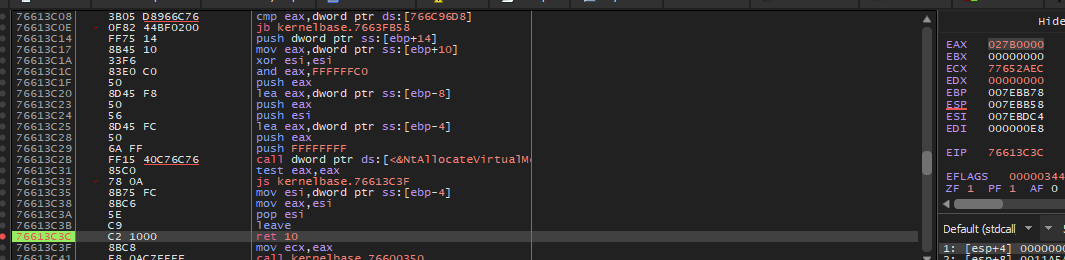
7- What is the protection of allocated memory?
After jumping to VirtualAlloc and running it to ret instruction we will see that eax holds a memory address and this is the address of allocated region which is 027B0000. Then we can follow this address in Memory Map, and we will see that the protection of this space is ERW

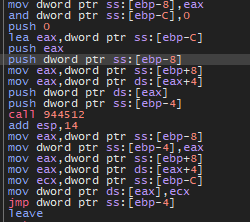
8- What assembly instruction is used to transfer execution to the shellcode?
After VirtualAlloc, we will see that eax which contains the address of allocated memory will move to [ebp-8] and then move to eax again and at the end will move to [ebp-4] and then jump to this location using jmp dword ptr ss:[ebp-4]
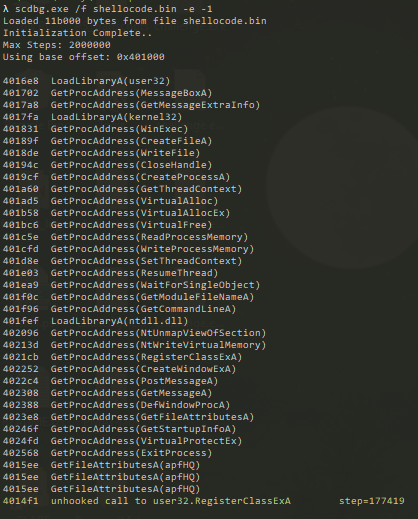
9- What is the number of functions the malware resolves from kernel32?
After that we can dump the sell code into a file and deal with it using scdbg by running this command
scdbg.exe /f shellocode.bin -e -1
We will find that the shell code will load DLLs with LoadLibraryA and get APIs with GetProcAddress. And if we count the APIs loaded from Kernel32 we will find that the shell code will get 16 APIs
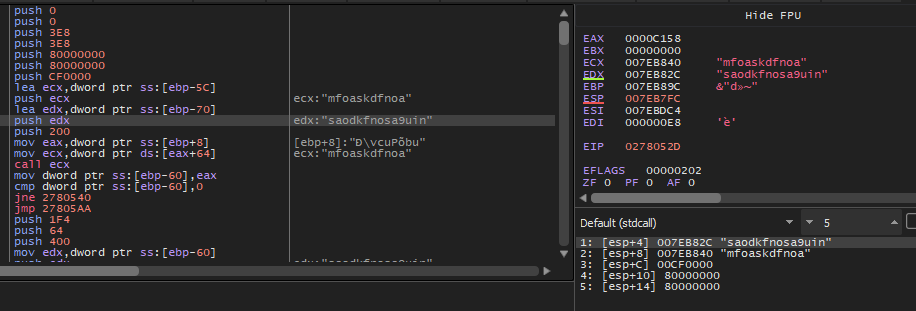
10- The malware obfuscates two strings after calling RegisterClassExA. What is the first string?
If we go to RegisterClassExA by CTRL+G in x64dbg and stepping into the code after it, we will see that the malware will that the malware will store 2 srings in the stack the first one is saodkfnosa9uin
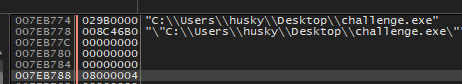
11- What is the value of dwCreationFlags of CreateProcessA?
As we did in the above question we will go to CreateProcessA in the code and get the value of the dwCreationFlags, according to msdn these flags is the sixth parameter
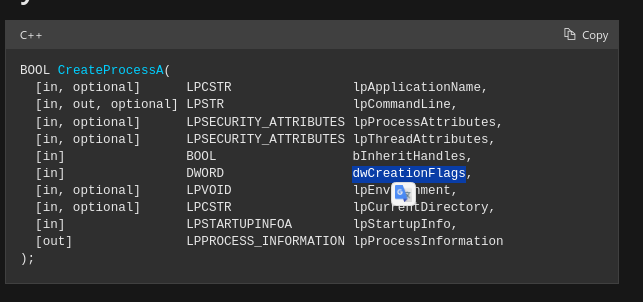
and the value of it is 08000004 which means that CREATE_SUSPENDED
12- Malware uses a process injection technique. What is the name of it?
After the malware creates a process in a suspend mode the malware will free the memory space of this process using VirtualFree with free type 8000
And the malware will use APIs like NTWriteVirtualMemoy and WriteProcessMemory to write a PE content in this space.
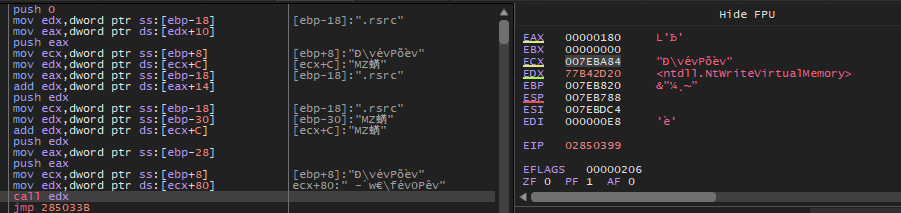
And then resume process with ResumeThread API.
This technique is a popular technique called Process Hollowing, and in this technique malware removes code in an executable file (VirtualFree) and replaces it with malicious code(WriteProcessMemory) to evade detection.
13- What is the API used to write the payload into the target process?
As we see above the malware use WriteProcessMemory to inject the malicious code.
References:
-
Report Discussing “Stack Strings”: https://www.archcloudlabs.com/projects/loadlibrary-analysis/
-
Process Hollowing: https://www.techtarget.com/whatis/definition/process-hollowing
